Small business owners face numerous challenges, but data security and fraud prevention may be some of the scariest. They can cause large-scale harm to even the smallest of enterprises. Scammers and bad actors can steal credit card information, PINs, and security codes to make unlawful transactions. A data breach at your small business can also lead to Social Security number theft, identity theft, tax ID theft, data mining, and even a loss of control over your accounts.
Some might believe larger organizations are the only ones at risk for a data breach, but it also affects small businesses. In fact, according to the Association of Certified Fraud Examiners, small businesses had the highest median loss of $150,000, compared to larger organizations.
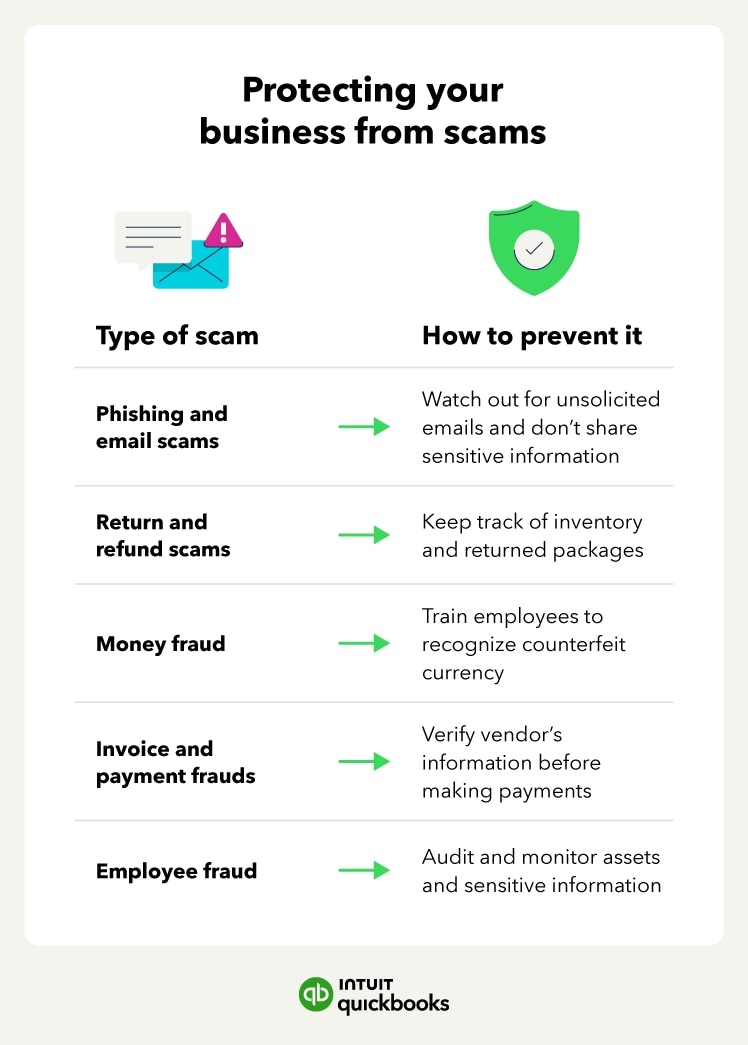
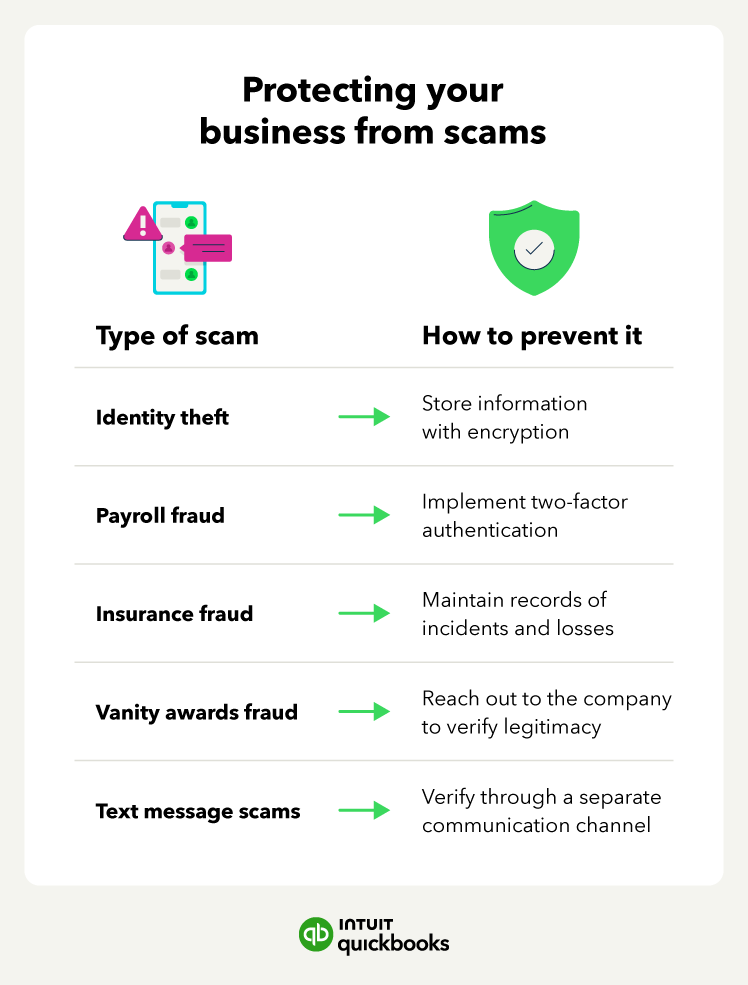
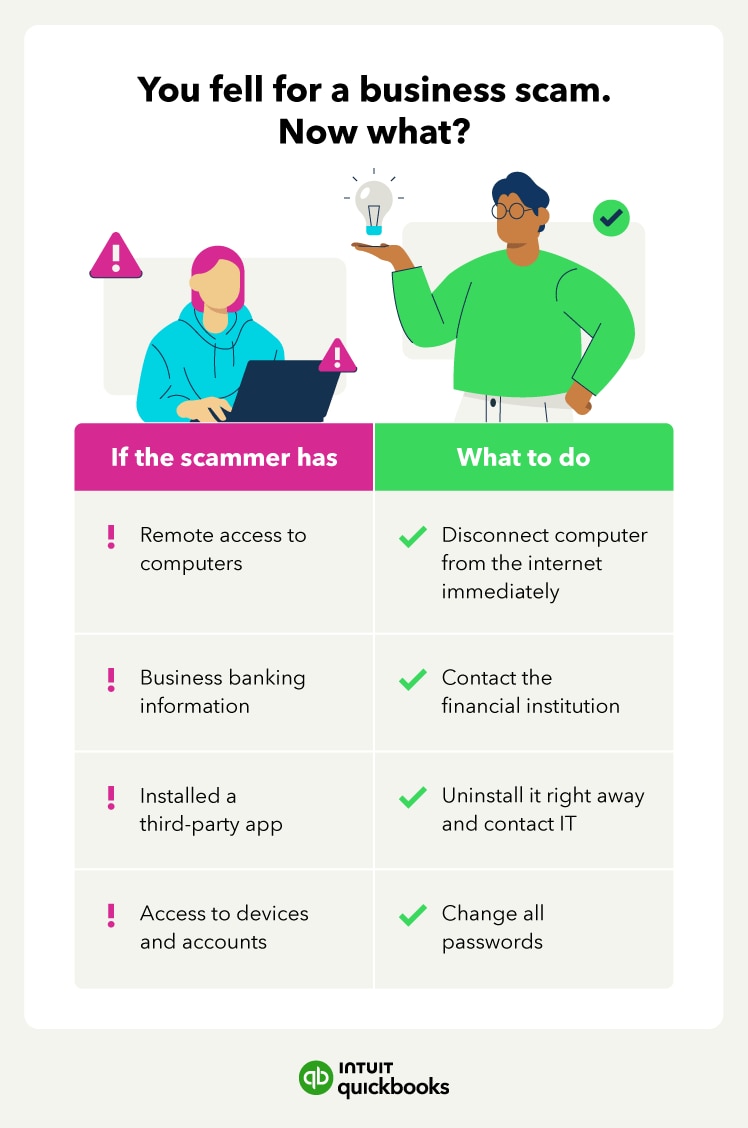
In this article, learn how to protect your business from business fraud and what to do in the case of a security breach.